We’re used to website names ending in .com, .org, .net, and so on. Recent years have seen new domain extensions appear, such as .aero, .club, and others. These are known as top-level domains (TLDs), and the list, already long, gets new additions every now and then. Google announced in May that eight more domains were available, two of these indistinguishable from popular file extensions: .zip and .mov. The move has been met with criticism from IT and infosec experts, as it pretty much guarantees confusion, a link handling mess, and new phishing patterns.
How to confuse .zip and .zip
ZIP and MOV files have been around for decades: .zip is the de facto archiving standard, and .mov is one of the most popular video containers. Google is aiming these new MOV and ZIP domains at techies, but in fact both are available to anyone and for any purpose.
Now, only context can help you figure out if a ZIP or MOV is a website or a file when you come across, say, update.zip. However, context is something humans can grasp, but not computers, so a reference like that could cause issues in all kinds of apps, such as Twitter:
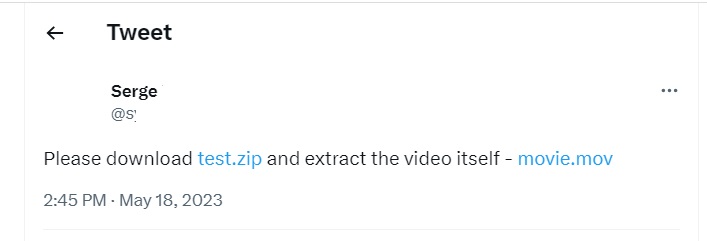
The tweet clearly refers to files, but Twitter turns the file names into web links. If someone registers the domains test.zip and movie.mov, those who click on the file links may fall victim to some a specific kind of phishing scheme.

Security researcher mr.d0x found another way to exploit the .zip domain for phishing. The technique he described, dubbed file-archiver-in-the-browser, involves the use of sites that imitate the interface of archiver utility. The user, believing that he is opening a .zip file, is actually redirected to the site of the same name and instead of a file list he sees URLs that can lead anywhere. For example they can hide a link to download an executable malware, or lead to a request for working credentials to access some document. The same document also describes an interesting delivery mechanism using Windows File Explorer. If the attacker manages to convince his victim to search for a non-existent .zip file, File Explorer will automatically open a site on the domain of the same name.
The phishing threat is already real, with some .zip phishing sites that exploit the Windows update theme having been spotted.
Not that this is the first time we’ve seen confusion similar to this. One of the original domains, .com, is also a legitimate extension for executables actively used in MS-DOS (and older versions of Windows), while the .sh extension used for Unix scripts is identical to the TLD for the British Overseas Territory of Saint Helena, Ascension and Tristan da Cunha. Still, it is ZIP and MOV, which are popular among the not-so-technical audience, that have the potential to cause issues to both users and system administrators. Even if you forget about phishing for a moment, situations like the one described in the tweet above could occur in dozens of apps that automatically process text and highlight links. Therefore, at any moment, any text that contains a file name could turn into text that contains a hyperlink to an external website. A phishing scheme or not, this could at the very least cause inconvenience if not bewilderment. Visit financialstatement.zip to see for yourself.
Tips for users
The advent of the ZIP and MOV domains won’t lead to drastic change in the phishing and online scam ecosystem — it will only add one more weapon to hackers’ already-vast arsenal. Therefore, our customary anti-phishing tips remain unchanged: study any links closely before clicking; beware of attachments and URLs in unsolicited e-mail; don’t click suspicious links; and be sure to use proper security on all your devices — even smartphones and Macs.
Tips for administrators
Some users are likely to ignore the advice above, so, depending on how your organization operates, you may need to set up separate security rules for .zip and .mov domain names. Possible measures include more stringent link scanning or even completely blocking users from visiting websites in these domains on corporate computers. This would not be without precedent: the .bit domain was widely blocked and gradually died out due to a deluge of malicious links in 2018–2019.
The appearance of the ZIP and MOV domains is an excellent occasion to conduct — or repeat! — infosec training for employees (with a focus on phishing detection).
We recommend that IT administrators test any key business systems that process links to see how these handle .zip and .mov websites, and if the use of ZIP files is accompanied by any undesirable effects. Mail systems, corporate instant messaging apps, and employee file-sharing services should be monitored especially closely, as these are where confusion is most likely to reign. Undesirable features, such as automatic creation of links based on certain name patterns, can be disabled for ZIP and MOV or across the board.
 phishing
phishing

 Tips
Tips