Cyberattacks are becoming increasingly common. Attacks happen to companies big and small, and often, hackers leak sensitive or private information. An estimated 668 data breaches took place in the U.S. in 2018, with more than 22 million records exposed, according to Statista. Data breaches pose serious risks to companies, vendors and customers, but there's an even bigger threat taking over the cybersphere: advanced persistent threat, or APT. We'll explain what APT is, what the warning signs are and how you can safeguard your company and its data.
What Is an Advanced Persistent Threat (APT)?
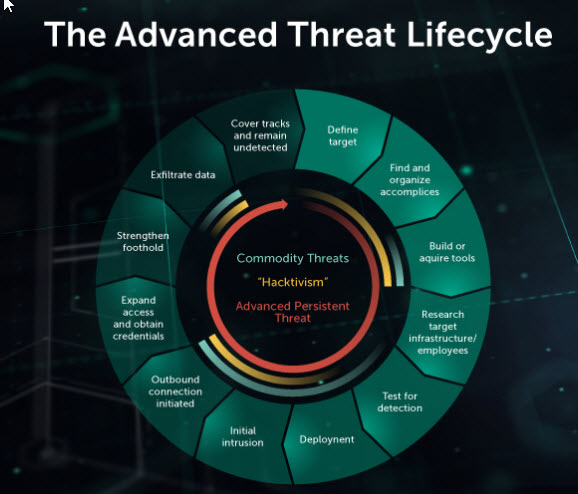
An APT is a long-term attack meant to locate and exploit highly sensitive information. A hacker gets into your computer network and spends a lot of time inside, monitoring movements, key users and data. Hackers work hard to remain undetected and may use sophisticated tools to do so.
These attacks aren't random. Hackers carefully research and target victims. These victims typically include larger organizations or even governments that deal with top-secret data, such as military plans, financial data or patents.
It's important to note that hackers may initiate attacks and use targeting methods that aren't advanced or persistent. Some actors sacrifice persistence for stealth, hoping the undetectable nature of their tactics can hide their efforts and reduce their need to launch persistent attacks. Others abuse administrative tools instead of using advanced, bespoke tools in the initial phase of an attack. The evolving nature of the ways attacks are carried out highlights the importance of using tested, trustworthy security software.
5 Warning Signs of APT
These attacks can be highly sophisticated and difficult to detect. How do you know if your company is the victim of APTs, especially considering that cybercriminals go to such lengths to remain untraceable? A combination of warning signs can potentially alert you to an APT. However, it's also critical to partner with an expert cyber security provider and utilize purpose-built anti-APT tools to detect and eliminate clandestine attacks. Common warning signs include the following:
1) Targeted Spear-phishing Emails
Hackers need a way in, and often, they often use emails as their entry points. They choose subjects that are likely to pique the interest of the employees they target, based on reconnaissance that they carry out before the attack. The messages might include an infected attachment or a link that downloads a program that provides access to your system.
These are called spear-phishing scams because of their highly targeted nature. They differ from typical phishing scams, which are distributed indiscriminately, are not personalized and try to trick large numbers of people into sharing personal information or data. Spear-phishing targets specific people at specific companies, and spear-phishers use their targets' personal information to appear more trustworthy and lend credibility to their messages. Any emails sent to high-level business executives with attachments from unknown people are red flags. It’s vital to make staff aware of the dangers of phishing and the risks associated with opening attachments and clicking on links in unsolicited messages.
2) Odd Logins
Track and evaluate logins on your network. If there are lots of logins that take place after work hours, or there are other unusual login patterns, it's a cause for concern. This is particularly true if those logins are people in executive roles with high-level access inside your network. Cybercriminals might be in foreign countries on the other side of the world, which can account for the unusual timing. They also try to operate when they know few, if any, people are in your office to catch and stop the suspicious activity.
3) Widespread Backdoor Trojans
Hackers often deploy backdoor Trojans to maintain access to computers. These are software programs that let hackers connect remotely to computers in compromised networks and send or receive commands. They're like leaving a back door open, so there's always a way in, even if login credentials change.
4) Information Moved
Hackers are in your system for a reason: they're after specific information. Watch for large batches of information moving around. Maybe files have shifted or data have moved from server to server. Look for data moving between computers on the same internal networks and for data moving to external computers. Keep an eye out for unusual connections, including connections to external resources.
5) Data Clumped and Ready for Export
Look for large files that aren't where they should be. Often, hackers group and compress data in one place before exporting it out of your system. This process makes it easier for them to move larger amounts of data at a time. Another sign that hackers are preparing to export data bundles is that the compressed data appear in an archive format your company typically doesn't use. Pay close attention to file extensions of bundled data.
Tips to Prevent APT
While APTs are sophisticated, your company can take measures to prevent them. Use these four tips to protect against APTs.
Educate All Employees About Phishing Scams
Many APTs start with a fraudulent email that gains access to your system. Deploy a training program that teaches employees what to look for, what to do and who to notify if they spot something suspicious. Stopping an attack before it starts is the best way to mitigate risks.
Make Sure All Security Patches Are Installed
APT hackers look to exploit any weakness in your system, which is why it's so crucial to run updates on all cybersecurity programs. If you avoid or delay updates and patches, you're leaving your company vulnerable to attacks.
Better Secure Your Most Sensitive Data
Consider taking additional safety measures with your most sensitive information. Don't automatically assign administrator rights to staff accounts if they don't need them. Limit access to and editing capabilities for data to reduce the likelihood of accidental changes. Take steps to make your most profitable data the most difficult to find and copy.
Work With a Cybersecurity Company
Does your company deal with sensitive material? You need a cybersecurity company with experiencing dealing with APT. This type of company can access your needs, deploy safety measures and actively monitor your digital footprint to ensure the most comprehensive security possible.
APTs can be extremely destructive to a company. If you believe your company is at risk, the best way to mitigate those risks is with an experienced cybersecurity company. Look for one that offers both APT Intelligence Reporting and the support you need to identify and stop threats.
Related articles and links:
- What is Advanced Persistent Threat?
- What is Cyber Security?
- What is Cybercrime: Risks and Prevention
- How to Avoid Most Types of Cybercrime





