Overview
We conduct a comprehensive assessment of industrial environments: uncovering weaknesses in ICS, OT, and networked devices, evaluating configurations and access paths, and mapping vulnerabilities to reveal actionable risks — all while keeping systems fully operational
HOW IT WORKS
Kaspersky ICS Security Assessment in action
ICS Security Assessment goes beyond standard security audits, combining remote analysis with on-site evaluation. By assessing systems on-site, it uncovers hidden risks and delivers actionable insights without disrupting operations
Define the project scope, objectives, and constraints. Coordinate planning with the customer, aligning expectations for a smooth, risk-aware assessment.
KEY FEATURES
Security assessments for OT/ ICS

Analysis of network traffic
Passive collection and analysis of OT network traffic for discovering vulnerable protocols and communication issues

Analysis of ICS hosts
Network access control, patch management, administrator access control, I/O port access control, and event collection.

Industrial solution software
Open source intelligence, kiosk mode escape, user authentication, patch management analysis

Analysis of basic level devices
Patch management and configuration of software analysis, review of installed firmware and hardware

Analysis of network equipment
L2, L3 network schemes review and network devices configuration analysis

Attack development
Demonstration and exploitation of the discovered vulnerabilities on previous stages
Reduce ICS threats. Share project details with experts
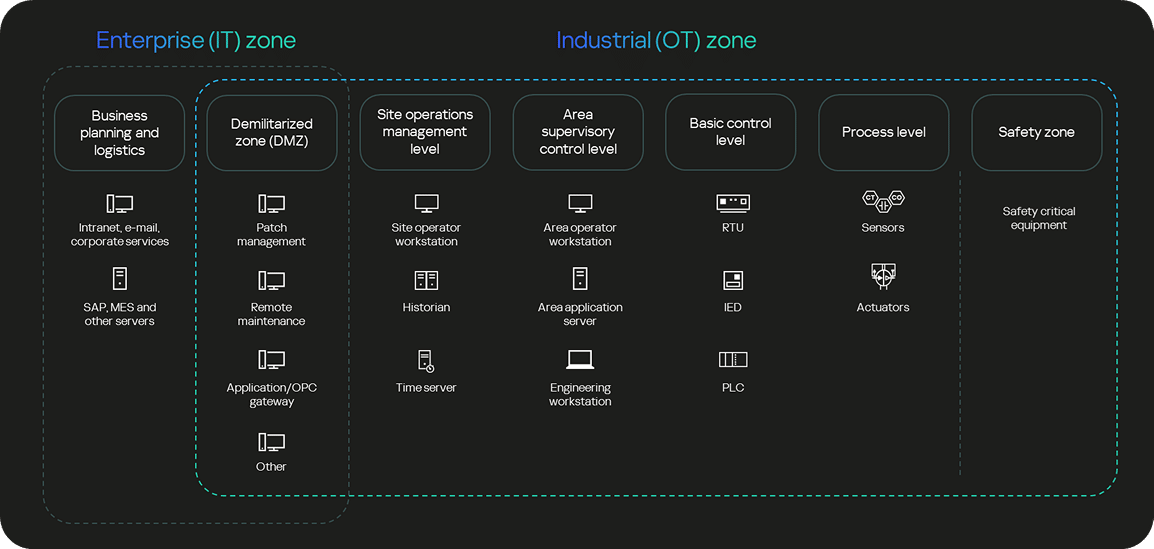
Purdue reference model
Our approach to industrial security assessment is based on the Purdue Reference Model. It leverages the defined Purdue levels to pinpoint and assess attack vectors across IT and OT. This clarity drives risk prioritization and informs targeted mitigation strategies.
DELIVERABLES
Insights that strengthen operations
Each assessment delivers an executive summary for leadership and a technical report for engineers—bridging strategy and execution through clear, actionable intelligence.

Threat modeling & risk focus
Prioritized vulnerabilities and potential impacts on technological processes.

Exposed attack surface
Mapped exposures, attack paths, and consequences for informed defense.

Intelligence & visibility
Detailed system and vulnerability data to enhance detection and response.

Secure configuration
Validated security measures and system hardening recommendations for operational safety.
RELATED SERVICES




