Amid a sharp drop in the number of malicious mass mailings, spam actors are learning new ways to bypass spam filters to succeed in their attacks.
According to Kaspersky Lab’s “Spam and phishing in Q1 2017” report, the world's largest spam botnet, Necurs, demonstrated a relative decline in its fraudulent mailshot traffic. In December 2016, Kaspersky Lab’s spam traps detected over 35 million fraudulent mailshots but in March 2017 that number fell to almost 7,000.
The Kaspersky Lab spam report also identified the following trends in the first quarter of 2017:
- Global share of spam amounted to almost 56% of Q1 email traffic on average, compared to 59.9% in Q4 2016.
- Total amount of malware attachments in email traffic decreased by 2.4 times, compared to the previous quarter.
- More than half of all phishing attacks targeted the financial sector, including banks (almost 26%), payment systems (over 13%) and online shops (almost 11%).
“At the beginning of 2017 we witnessed a number of changes in spam flows, including a sharp drop in the number of malicious mass mailings from the world's largest spam botnet. Amid this, the spam threat actors are gaining new footholds in anti-detection tricks and techniques, capturing legal communication platforms and password-protected attachments. Most likely this trend will continue, with documents protected by passwords considered trusted in the eyes of a victim. Moreover, these documents and not able to be scanned by the IT security solution,” said Darya Gudkova, Spam Analyst Expert at Kaspersky Lab.
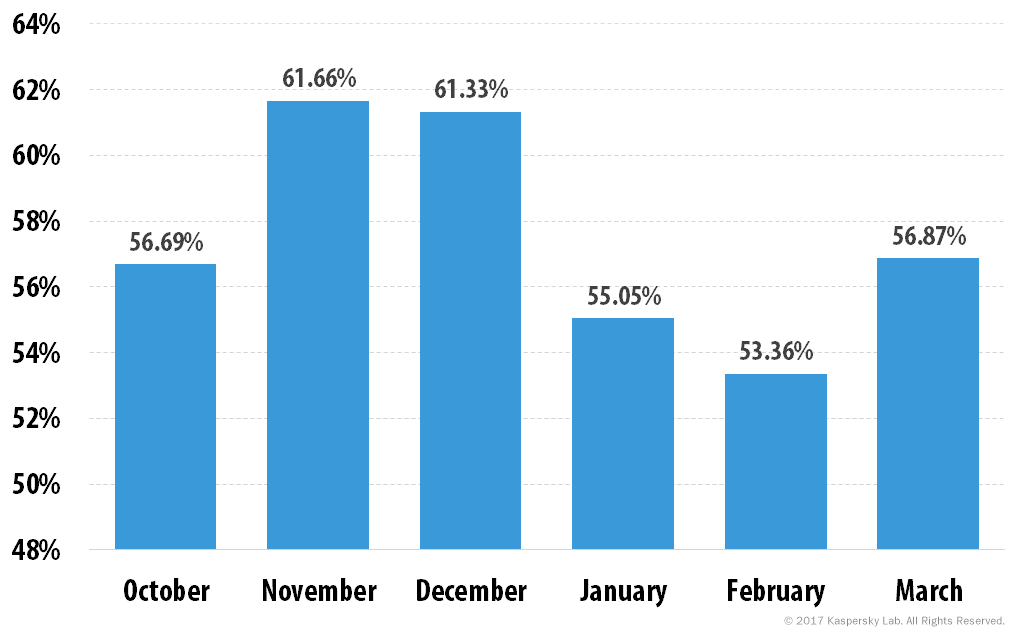
Percentage of spam in global email traffic, Q4 2016 and Q1 2017
The fall of the Necurs botnet
In 2016, Kaspersky Lab researchers identified a sharp increase in spam with malicious attachments, primarily with encryptors. Most of this traffic came from the Necurs botnet, which is currently considered the world's largest spam botnet. However, at the end of December 2016, the network practically stopped, and not just for the Christmas holidays. The botnet’s spam was at a very low level for almost the entire first quarter of 2017.
Apparently, criminals were scared by increased hype around the encryptors and decided to suspend mass mailings. However, this decision is unlikely to result in the extinction of this attack vector.
Malicious emails with password-protected files
In the first quarter of 2017 spammers tended to complicate their anti-detection techniques in multiple ways. Among others, cybercriminals packed the malware in password-protected files. Once a user received the email, spammers provoked victims to open and archive in the usual way. They forged emails under order notifications from large retail stores, through various transactions and CVs, or promised large sums of money. Frequently, the emails were sent on behalf of various existing small and medium-sized businesses, with all of the signatures and contacts proving the reliability of the sender.
Once a victim opened the documents, a malicious script was activated and downloaded malware onto computers. The malware payloads were diverse and included ransomware, spyware, backdoors, or a new modification of the notorious Zeus Trojan.
Spam through legal services
Modern email spam filters effectively cope with the problem of detecting spam sent via emails. This provokes spammers to look for new channels to bypass the barriers. They are increasingly focusing on messengers and social networks to disseminate their advertising and fraudulent offers.
Private messages are usually supported with notifications to the recipient’s email. In this case, the email headers will be considered legitimate, unlike traditional email spam. This means that it will be possible to detect spam only by analysis of the message content. This is a much more difficult task, especially given the legal source of information and if the service address is added to the recipient’s trusted list.
Advice
Home users are recommended to use a security solution able to recognize and block malicious attachments and filter spam in desktop email apps, such as Kaspersky Total Security.
Kaspersky Lab recommends that businesses use security solutions with a dedicated functionality aimed at malicious attachments and spam. Small businesses can protect themselves with Kaspersky Small Office Security, which spots and blocks emails with spam. Larger companies can benefit from real-time cloud-assisted anti-spam scanning of all messages on Microsoft® Exchange and Linux-based email servers — with the Kaspersky Security for Mail Server application included with Kaspersky Total Security for Business.
Read more about spam and phishing in early 2017 on Securelist.com




