In November 2022, researchers at universities in the U.S. and Canada demonstrated a method of Wi-Fi device localization using inexpensive and easy-to-find equipment. The attack proof-of-concept was dubbed Wi-Peep, as it can be used to peep on devices communicating with each other via Wi-Fi. The research offers new insight into certain features of Wi-Fi networks, and the potential risks of device-localization. We should start by saying that the risks aren’t too high — an attack looks like something out of a Bond movie. But that doesn’t make the research any less interesting.
Wi-Peep attack features
Before looking at the report in detail, let’s consider a real-life attack. Attackers fly a mini-quadcopter with the most inexpensive microcomputer on board around a target building, collecting data to obtain a map of wireless devices inside with reasonable accuracy (±1.5 meters under ideal conditions). But why would they? Well, let’s imagine it’s a bank or a top-secret laboratory whose security systems are equipped with Wi-Fi modules. And there’s your “why”: their location could be of huge practical interest to attackers planning physical penetration.
Simplified Wi-Peep attack scheme. Source.
So how do researchers imitate something like that?…
The Wi-Peep attack exploits two important features of absolutely any Wi-Fi device, from ancient wireless modules from 20 years ago to the most modern. The first is the power-saving mechanism in Wi-Fi devices. The Wi-Fi module, say, in a smartphone can preserve battery by shutting down the wireless receiver for short periods of time. A wireless access point needs to consider this mode of operation: your router can accumulate data packets for a specific device, then transmit them all at once when it signals it’s ready again to receive a transmission.
For a successful attack, a potential spy would need to obtain a list of MAC addresses — unique device IDs whose locations would be determined later. Devices in the same home, office, or hotel are usually connected to a shared Wi-Fi network, the name of which is no secret. It turned out that it’s possible to send a fake data packet, ostensibly from this shared wireless network, informing all connected devices that the access-point buffer has accumulated some data destined for them. In reply to this signal, the devices send responses which, when analyzed, reveal the unique MAC addresses of all network devices almost instantly. But there’s a simpler way: eavesdrop on wireless radio traffic; however, this takes more time: according to the researchers you need to accumulate data in passive mode for 12 hours.
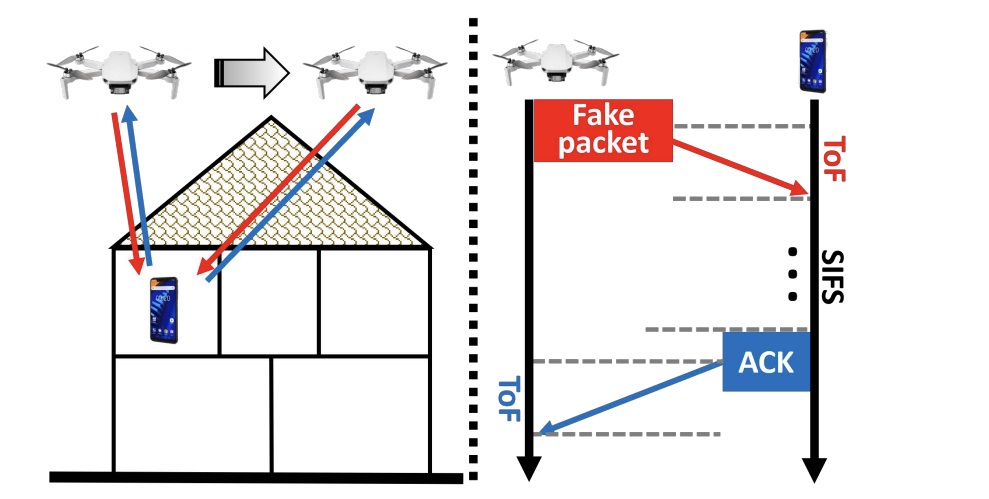
The second exploitable feature of wireless data exchange was provisionally named Wi-Fi Polite. That name was assigned by the authors of an earlier 2020 study. In a nutshell, the essence of the feature is this: a wireless device always responds to an address request from another device, even if they’re not connected to a shared Wi-Fi network, and even if the request isn’t encrypted or is malformed. In response, the Wi-Fi module sends a simple confirmation (“Data from you received”), but that turns out to be sufficient to determine the distance to the responding device. The response time for receipt of such a packet is strictly regulated, and is 10 microseconds. A potential attacker can measure the time between sending a request and receiving a response, subtract those 10 microseconds, and get the time taken for the radio signal to reach the device.
What does that give? Moving around a stationary wireless device, we can determine its coordinates with a fairly high degree of accuracy, knowing our own location and the distance to the object of interest. Much of the research is devoted to overcoming the many difficulties of this method. The signal from the Wi-Fi radio transmitter is constantly reflected by walls and other obstacles, making it difficult to calculate the distance. In fact, that standardized response time should be 10 microseconds, but it actually varies from device to device — ranging from 8 to 13 microseconds. The geolocation accuracy of the attackers’ Wi-Fi module itself also has an effect: it turns out that even the precision of geopositioning systems (GPS, GLONASS, etc.) isn’t always enough. Although the resulting data contains a lot of noise, if enough measurements are made, relatively high accuracy can be achieved. That means if you make tens of thousands of readings, you get a positioning accuracy with an error in the range of 1.26 to 2.30 meters — on the horizontal plane. On the vertical, the researchers were able to determine the exact floor in 91% of cases, but nothing more.
Low-cost sophisticated attack
Although the system for determining the coordinates of wireless devices turned out to be not very accurate, it’s still of interest — not least because the equipment used by the researchers is dirt-cheap. Theoretically, an attack can be carried out by a potential spy in person, simply by slowly walking around the target object. For added convenience, the researchers used a cheap quadcopter fitted with a microcomputer based on the ESP32 chipset and a wireless module. The total cost of this reconnaissance kit (excluding the cost of the quadcopter) is less than US$20! What’s more, the attack is virtually impossible to trace on the victim’s device. It uses the standard capabilities of Wi-Fi modules, which cannot be disabled or at least modified in terms of behavior. If communication between the victim’s device and the attackers’ microcomputer is possible in principle, the attack will work. The practical range of data transmission over Wi-Fi is tens of meters, which in most cases will suffice.
Fuzzy implications
If we assume the attack is doable in real life, is the data obtained of any use? The researchers propose several scenarios. First and most obviously, if we know the MAC address of the smartphone of a specific individual, we can roughly track their movements in public places. This is possible even if their smartphone is not connected to any wireless networks at the time of the attack. Second, creating a map of wireless devices in a secure building (a competitor’s office, bank premises) for a subsequent physical attack is an entirely realistic scenario. For example, attackers can determine the approximate location of surveillance cameras if these use Wi-Fi for data transmission.
There are also less obvious benefits from collecting such data. You could, for instance, collect information about the number of Wi-Fi devices in a hotel to estimate how many guests there are. Such data may be of interest to competitors. Or, knowing the number of wireless devices could help determine if potential victims are at home. Even the MAC addresses themselves — without coordinates — are of some use: for collecting statistics about smartphone usage in a public place. In addition to spying and burglary, such methods are a threat to people’s privacy.
However, the immediate risk of such a method being deployed in practice is still quite low. This applies to all potential attacks and data collection methods for which you have to get close to the target object. It’s quite labor-intensive for one thing, meaning that few would do it on a mass scale, and for targeted attacks — other methods may be more effective. At the same time, scientific research helps to understand how minor features of complex technologies can be harnessed for malicious purposes. The researchers themselves note that the real benefit of their work will be if this small security and privacy risk is eliminated in future versions of wireless data transmission technologies.
For the time being, all we can recommend is to use an anti-drone system. It won’t help against Wi-Peep, but it will at least guard against being spied on from the air.
 espionage
espionage

 Tips
Tips