Admit it: you’ve been meaning to jump on the latest NFT reincarnation — Telegram Gifts — but just haven’t gotten around to it. It’s the hottest trend right now. Developers are churning out collectible images in partnership with celebs like Snoop Dogg. All your friends’ profiles are already decked out with these modish pictures, and you’re dying to hop on this hype train — but pay as little as possible for it.
And then it happens — a stranger messages you privately with a generous offer: a chance to snag a couple of these digital gifts — with no investment required. A bot that looks completely legit is running an airdrop. In the world of NFTs, an airdrop is a promotional stunt where a small number of new crypto assets are given away for free. The buzzword has been adopted on Telegram, thanks to the crypto nature of these gifts and the NFT mechanics running under the hood.
They’re offering you these gift images for free — or so they say. You could later attach them to your profile or sell them for Telegram’s native currency, Toncoin. You don’t even have to tap an external link. Just hit a button in the message, launch a Mini App right inside Telegram itself, and enter your login credentials. And then… your account immediately gets hijacked. You won’t get any gifts, and overall, you’ll be left with anything but a celebratory feeling.
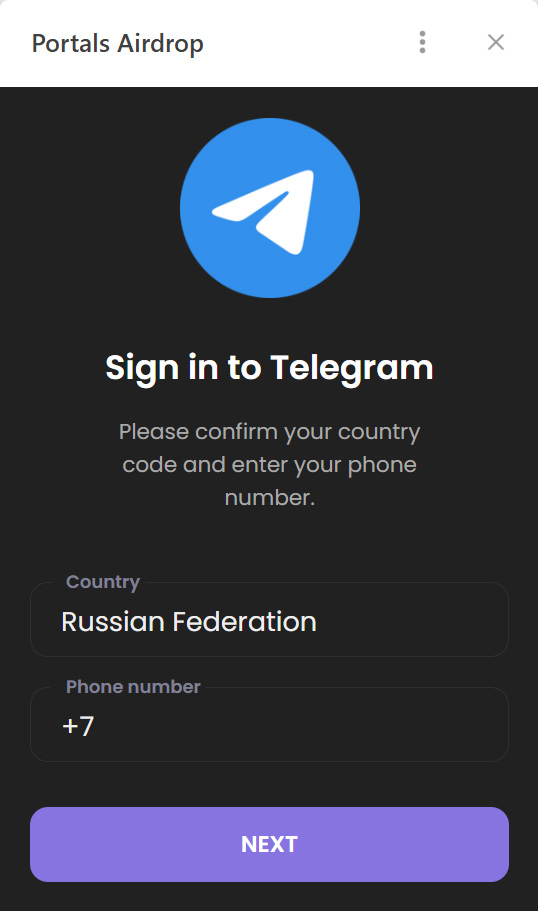
This is the first of the screens where, by filling in the fields, you receive a gift lose access to your Telegram account
Today, we break down a phishing scheme that exploits Telegram’s built-in Mini Apps, and share tips to help you avoid falling for these attacks.
How the new phishing scheme works
The principle of classic phishing is straightforward: the user gets a link to a fake website that mimics a legitimate sign-in form. When the victim enters their credentials, this data goes straight to the scammer. However, phishing tactics are constantly evolving, and this new attack method is far more insidious.
The bad actors create phishing Mini Apps directly inside Telegram. These appear as standard web pages but are embedded within the messaging app’s interface instead of opening in an external browser. To the user, these apps look completely legitimate. After all, they run within the official Telegram app itself.
This leads the victim to think, “If this app runs inside Telegram, there must be some kind of vetting process for these apps. Surely they wouldn’t let an obvious scam through?” In practice, it turns out that’s not the case at all.
How is this scheme even a thing?
A core security issue with Telegram Mini Apps is that the platform does almost no vetting before an app goes live. This is a world apart from the strict review processes used by Google Play and the App Store — although even there, obvious malware occasionally slips through.
On Telegram, it’s far easier for bad actors. Essentially, anyone who wishes to create and launch a Mini App can do so. Telegram does not review the code, functionality, or the developer’s intent. This turns a security flaw within a messaging service boasting nearly a billion global users into a global-scale problem. To make matters worse, moderation of these Mini Apps within Telegram is entirely reactive — meaning action is only taken after users start complaining or law enforcement gets involved.

This is a global operation, with phishing lures being distributed simultaneously in both Russian and English. However, the Russian version gives away a tell-tale sign of the scammers’ haste and lack of polish. They forgot to remove a clarification question from the AI that generated the text: “Do you need bolder, more official, or humorous options?”
In this case, the bait was “gifts” from UFC fighters: a giveaway of “papakhas” — digital gift images of the traditional Dagestani hat released by Telegram in partnership with Khabib Nurmagomedov. An auction for these items did take place, with Pavel Durov even posting about it on his X and Telegram (Khabib reposted these announcements but later deleted them after the auction ended). However, there were only 29 000 of these “papakhas” released, which wasn’t enough to satisfy all the eager fans. Scammers seized on the opportunity, assuring fans they could get the exclusive items for free. The phishing campaign was a targeted one — focusing on users who’d been active on the athlete’s channel.
How the scammers lull their victims
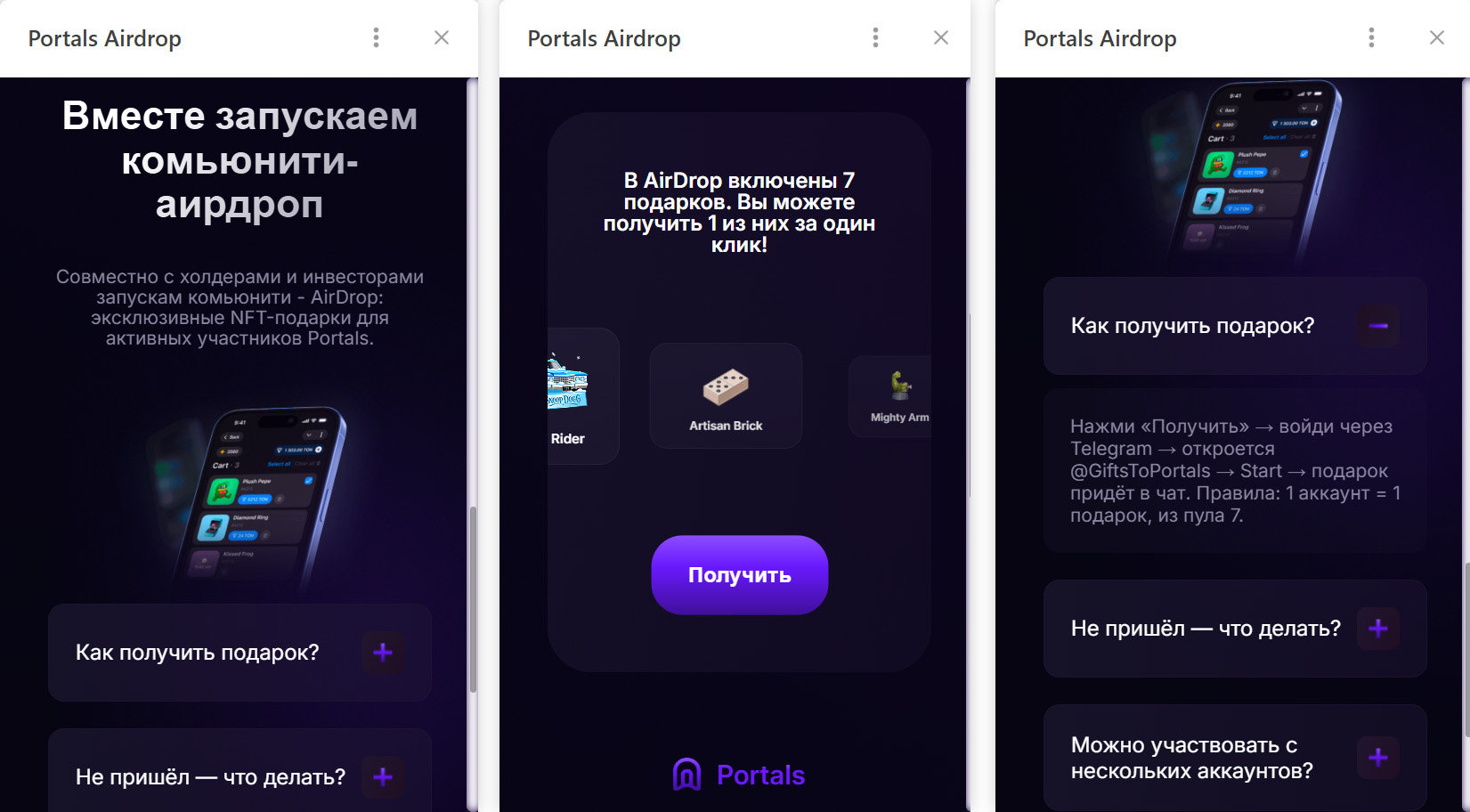
The criminals leveraged the name of the popular Portals platform — a legitimate service for games, apps, and entertainment within Telegram. They created a series of Mini Apps that were visually almost indistinguishable from the real ones, and promoted them as free giveaways — airdrops.

To add a veneer of authenticity, the scammers even listed the official Telegram channel for Portals in the phishing Mini App’s profile. However, the legitimate Portals Market bot has a different username: @portals
That said, the scam campaigns themselves show signs of being rushed and cutting design and copywriting costs — with obvious signs of AI involvement. Some of the messages contain leftover text fragments clearly generated by a neural network, which the scammers either forgot or couldn’t be bothered to edit.
How to protect your Telegram account from being hacked
The golden security rules are simple: stay vigilant, and learn the key hallmarks of these attacks:
- Verify the source. If you receive a link promising a giveaway from a celebrity or even Telegram itself but sent from an unfamiliar account or a dubious group, don’t click. Cross-check through the celebrity or company’s official channel to see if they’re actually running a promo like that.
- Inspect the account verification badge. Ascertain that the blue checkmark is real and not just an emoji status or part of the profile name. You can verify this by simply tapping that checkmark icon in the profile. If it’s a Premium emoji status, Telegram will explicitly tell you so. If a checkmark emoji is simply added to the profile name, tapping it doesn’t do anything. But if the account is genuinely verified, tapping the blue checkmark will bring up an official confirmation message from Telegram.
- Don’t be in a rush to authenticate in Mini Apps. Legitimate Telegram apps typically don’t require you to sign in again through a form inside the Mini App. If you’re prompted to enter your phone number or a verification code, it’s likely a phishing attempt.
- Look for signs of AI-generated text or design. Weird grammar, unnatural phrasing, or leftover neural network prompts within a message are a red flag. Scammers frequently use AI-powered generation to churn out text quickly and cheaply.
- Turn on two-step verification (your Telegram password). Do this right now in Settings → Privacy and Security → Two-Step Verification. Even if a scammer manages to get your phone number and SMS code, they won’t be able to access your account without this password. Obviously, never share your password with anyone — it’s meant only for you to sign in to your Telegram account.
- Use a passkey to secure your account. A recent Telegram update added the ability to securely sign in with a passkey. We’ve covered using passkeys with popular services and the associated caveats in detail. A passkey makes it nearly impossible for a malicious actor to steal your account. You can set one up in Settings → Privacy and Security → Passkeys.
- Store your password and passkey in a password manager. If you’ve secured your account with both a password and a passkey, remember that a weak, reused, or compromised password can still be the proverbial “spare key under the mat” for attackers — even if the “front door” is locked with a passkey. Therefore, we recommend creating a strong, unique password for Telegram and storing it — along with your passkey — in Kaspersky Password Manager. This keeps your credentials and keys available across all your devices.
- Install Kaspersky for Android on your smartphone. Its new anti-phishing technology protects you from phishing links embedded in notifications from any app.
What to do if your Telegram account was already stolen
The key is keeping calm and acting swiftly. You have just 24 hours to reclaim your account, or you risk losing it permanently. Follow the step-by-step guide to restoring access in our post What to do if your Telegram account is hacked.
Finally, a reminder that has become our classic mantra: if an offer looks too good to be true, it almost certainly is. Always verify information through official channels, and never enter your passwords or passkeys into unofficial apps or forms — even if they look legit. Stay vigilant and stay safe.
Want more tips on securing your messenger accounts and chats? Check out our related posts:
 messengers
messengers


 Tips
Tips