These days, spying on people has gotten far too easy. Anyone can buy stalkerware apps, which can look like parental control software or a smartphone antitheft solution. The classification may help developers avoid legal trouble; the software’s real purpose is to collect a great deal of highly sensitive information from devices without their users’ knowledge.
Although the legal status of stalkerware is gray, the use of such apps is not only unethical but also dangerous. We believe in countering the threat, in particular by raising awareness about it and any protective measures available to concerned citizens.
The scale of the scourge
Stalkerware apps’ features vary, but most enable total surveillance of the victim’s smartphone. Moreover, to install the app on the target device, the attacker simply needs to gain physical access to it once. Many people trust their partners enough to give them that access.
Among other things, stalkerware users can, without alerting their target in any way:
- Track a victim’s location;
- Read messages in messaging apps and social networks;
- View photos, videos, and other files on the device;
- Eavesdrop on telephone conversations;
- See everything typed on the keypad, including passwords and two-factor authentication codes.
Stalkerware typically hides itself from the list of installed programs and does not display any activity notifications.
Knowing their victim’s every move, an attacker can control, threaten, and psychologically pressure them. According to a 2017 report by the European Institute for Gender Equality (EIGE), seven of ten women affected by online stalking have experienced physical violence, sexual violence, or both at the hands of the perpetrator.
The scale of the problem continues to grow. For example, an Australian study on technology abuse and domestic violence showed that, since 2015, attackers have become far more likely to track the locations of current and former partners, and almost twice as likely to monitor them with cameras. The Centre Hubertine Auclert in France reports that one in five victims of relationship violence has encountered spyware. Germany also notes a rise in the use of stalkerware in recent years.
54,000 stalkerware victims in 2020
What has changed since 2019, when we teamed up with like-minded companies and nonprofits in the fight against stalkerware? Data from Kaspersky Security Network indicates almost 54,000 users worldwide were affected by stalkerware apps in 2020. Is that high or low? The figure in 2018 was almost 40,000, but in 2019 it topped 67,000.
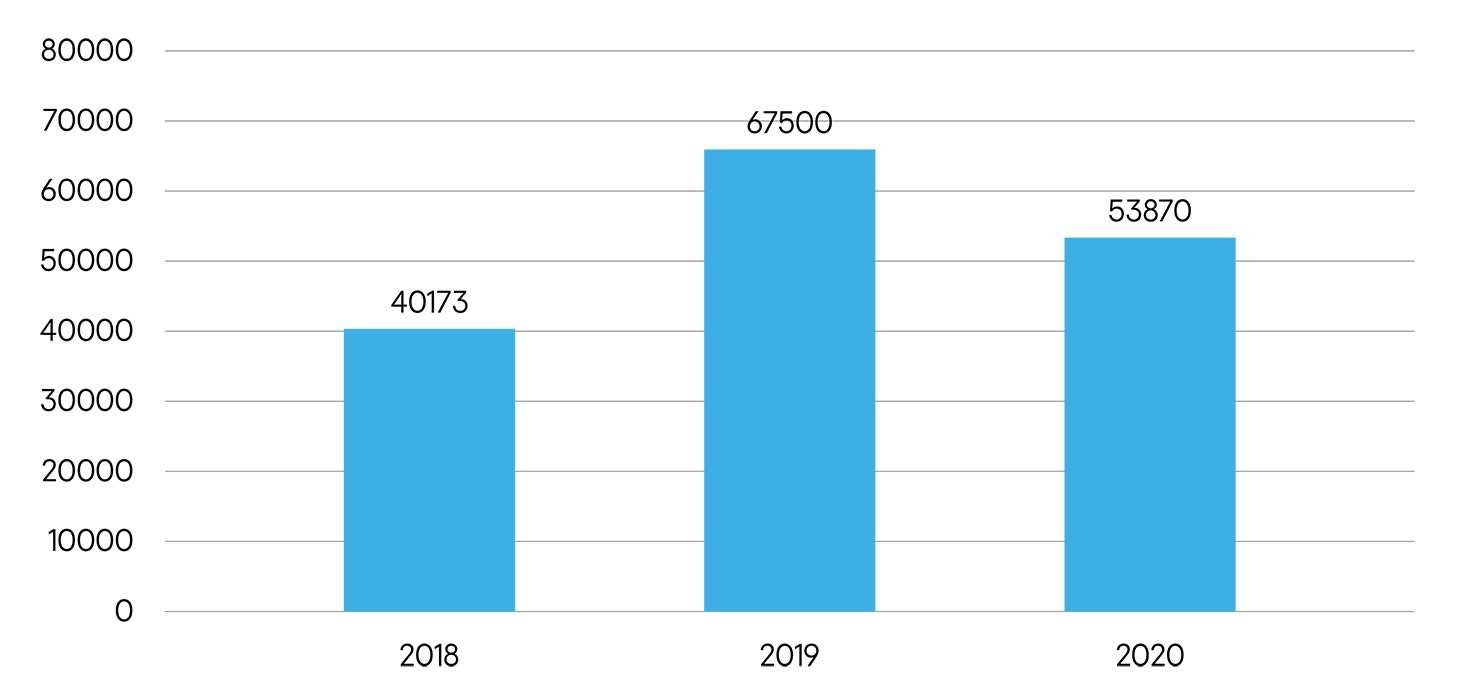
Unique users worldwide affected by stalkerware, 2018–2020. Source
This much is clear: The fight against online stalking is far from won. First, when it comes to threats of violence, 54,000 is a big number, however you slice it. Second, the pandemic and its consequences are factors, holding people house-bound in 2020 — and household members (spouses, roommates) are by far the most likely to use stalkerware apps. Isolation is likely to skew the numbers; with a victim stuck at home, a stalker may not monitor their smartphone’s whereabouts.
With that in mind, it is unsurprising that the yearly curve of users affected by stalkerware globally shows a decline in reports from March to June 2020. That period coincides with the beginning of worldwide lockdowns. Later, when many countries around the world began to ease restrictions, the numbers began to rebound and stabilize.
As for geography, our solutions most often detected stalkerware in Russia, Brazil, and the US, all of which landed in the Top 5 in 2019 as well. Among Asian countries, the problem was most acute in India, and the hardest hit in Europe were Germany, Italy, and the UK.
2020’s most common stalkerware families
As for stalkerware apps, the most common specimen in 2020 was the one our solutions call Monitor.AndroidOS.Nidb.a. Its developers allow the app to be resold under other names, so it is prominent in the market. The iSpyoo, TheTruthSpy, and Copy9 apps, for example, are all Nidb. Interestingly, until just a year ago, this stalkerware family was only the third most prevalent.
Another very popular piece of spyware is Cerberus, which is sold as antitheft smartphone protection and hides itself to avoid notice. What’s more, like genuine phone-finding apps, Cerberus has access to geolocation, can take photos and screenshots, and records sound.
Other high-ranking stalking apps include Track My Phone (which our solutions detect as Agent.af), MobileTracker (which enables remote control of the victim’s device), and the stalkerware program Anlost. The latter, like Cerberus, appears to be an antitheft tool, but it’s available on Google Play, which declared war on stalkerware last year, because it meets the store’s requirements.
How to detect stalkerware
One of the main problems with stalkerware is that it can’t just be found and removed. Removing stalkerware could alert an abuser that the victim is aware of being spied on. Some of the samples actually send a notification to the stalker, in which case deleting the app could escalate conflict and further endanger the victim.
But stalkerware can, and must, be detected — for starters, knowing you are being watched can lead you to take precautions or seek help. There are several ways to sniff out a spy.
- Keep an eye on battery and mobile data usage. Stalkerware runs in the background, sending constant streams of data to its server and eating up resources;
- Check which apps have been given dangerous permissions such as geolocation access or Accessibility (a set of Android features that lets an app control phone settings, read on-screen text, and more). If an unfamiliar app is using such permissions, it is likely to be stalkerware;
- Use a security solution that identifies and warns you about stalkerware. However, bear in mind that some types of stalkerware notify their operators if their target installs antivirus protection;
- Use TinyCheck, a solution designed to find stalkerware without its operator knowing.
You can learn more about the tools and techniques mentioned above and how effective they are on our blog.
How to reduce the risk of stalkerware infection
You can reduce the risk of someone sneaking stalkerware onto your devices, too:
- Never give your phone to anyone and, if possible, don’t even leave it unattended;
- Protect your device with a strong alphanumeric password that you never share with anyone;
- Block the installation of apps from third-party sources in your device settings, and use only the official app stores;
- Protect your device with a reliable mobile antivirus utility that detects and warns you about stalkerware.
 stalkerware
stalkerware

 Tips
Tips