With each passing year, the mobile malware landscape continues to evolve. It’s now driven by groups of criminals working to carry out large scale attacks and earn substantial profits. There has even recently been evidence of virus writing groups working together to push malware to a greater audience. So it seems the trend is clear: a mobile malware industry will continue to expand.
2013 In Figures
A look back over 2013 has us clearly seeing the tremendous growth that occurred in known cases of mobile malware. However, although malware reached an all-time high, so did Kaspersky Lab’s protection capabilities:
- In 2013, 3,905,502 installation packages were used by cybercriminals to distribute mobile malware. Overall in 2012-2013, we detected approximately 10,000,000
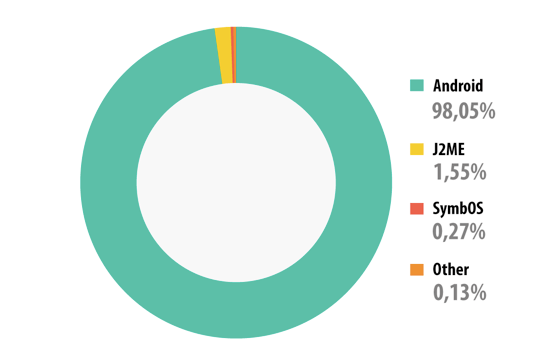
- Android remained a prime target for malicious attacks. 98.1% of all malware detected in 2013 targeted this platform.
- The majority of mobile malware still specialize on minor money theft using premium rate calls and messages. However, over the year, the number of mobile malware modifications designed for phishing, the theft of credit card information and money increased by a factor of 19.7.
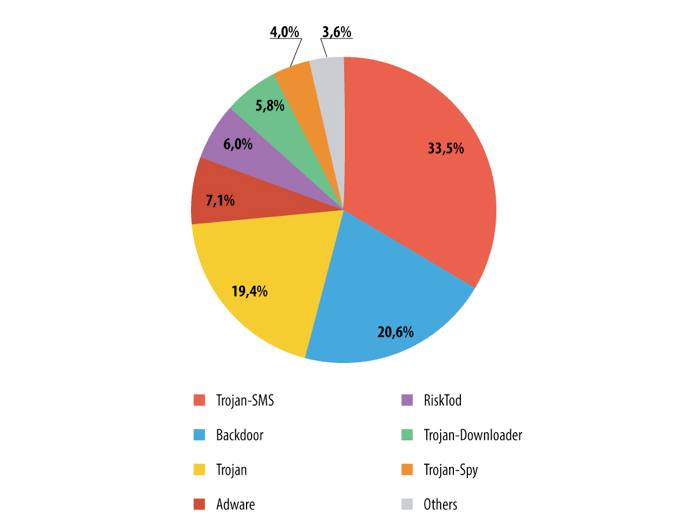
The distribution of mobile malware by category
Resistance to Protection and Capabilities
When it comes to creating malware, a leading consideration for cybercriminals is the ability for it to operate continuously on a victim’s device. The longer the device remains infected, the greater the chance for profit. This has led criminals to specifically focus on writing complex viruses which are difficult to find or remove:
- Android vulnerabilities are now used by criminals to bypass the code integrity check when installing an application (vulnerability Master Key), to enhance the rights of malicious applications, considerably extending their capabilities and making them more difficult to remove.
Android vulnerabilities are now used by criminals to bypass the code integrity check when installing an application
- Malicious code is also now embedded in legitimate programs to hide signs of infection. As a result, a copy of Angry Birds installed from an unofficial app store or downloaded from a forum could easily contain malicious functionality.
- Attacks on Windows XP allowed mobile malware to infect PCs after victims connected their smartphone or tablet.
Trend of the Year: Mobile Banking Trojans
Along with these complex attacks also came a standout trend: a rapid rise in Android banking Trojans. At the beginning of the year we knew of only 67 banking Trojans, but by the end of the yea,r there were already 1321 unique samples. Mobile banking Trojans are even running together with Win-32 Trojans to bypass the two-factor authentication now.
Mobile malware is showing no sings of slowing down anytime soon, as new programs continue to appear and cases of infection soar. But as we expect to see continued growth in programs that evade detection and removal, Kaspersky Lab will remain dedicated to providing you with protection you can trust.
 device security
device security




 Tips
Tips