We all know what it means to “read between the lines” in a figurative sense, but before we used modern technology to communicate with one another, people sometimes took it literally, such as by writing secret messages in invisible ink between the lines of a seemingly normal letter.
The technique, whereby the author of a message hides secret information inside something that looks innocent on the surface, is known as steganography, and it is almost as old as writing itself. Unlike cryptography, which scrambles the message to make it unreadable without the decryption key, the purpose of steganography is to conceal from prying eyes the very existence of the message. As with many other information-handling methods, steganography is now used in digital technologies, too.
How does digital steganography work?
A secret message can be hidden in almost any digital object, be it a text document, license key, or even file extension. For example, the editors of Genius.com, a website dedicated to analyzing tracks by rap artists, used two types of apostrophes in their online lyrics that, when combined, made the words “red handed” in Morse code, thereby protecting their unique content from being copied.
One of the most convenient “containers” for steganographers happens to be media files (images, audio, video, etc.). They are usually quite large to begin with, which allows the added extra to be meatier than in the case of, say, a text document.
Secret information can be written in the file metadata or directly in the main content. Let’s take an image as an example. From the computer’s point of view, it is a collection of hundreds of thousands of pixels. Each pixel has a “description” — information about its color.
For the RGB format, which is used in most color pictures, this description takes up 24 bits of memory. If just 1 to 3 bits in the description of some or even all pixels are taken up by secret information, the changes in the picture as a whole are not perceptible. And given the huge number of pixels in images, quite a lot of data can be written into them.
 |
 |
The left-hand image has no hidden message; the right-hand image contains the first 10 chapters of Nabokov’s Lolita
In most cases, information is hidden in the pixels and extracted from them using special tools. To do so, modern steganographers sometimes write custom scripts, or add the required functionality to programs intended for other purposes. And occasionally they use ready-made code, of which there is plenty online.
How is digital steganography used?
Steganography can be applied in computer technologies in numerous ways. It’s possible to hide text in an image, video, or music track — either for fun or, as in the case above, to protect a file from illegal copying.
Hidden watermarks are another good example of steganography. However, the first thing that comes to mind on the topic of secret messages, in both physical and digital form, is all manner of secret correspondence and espionage.
A godsend for cyberspies
Our experts registered a surge in cybercriminal interest in steganography 18 months ago. Back then, no fewer than three spyware campaigns swam into view, in which victims’ data was sent to C&C servers under the guise of photos and videos.
From the viewpoint of security systems and employees whose job it is to monitor outgoing traffic, there was nothing suspicious about media files being uploaded online. Which is precisely what the criminals were counting on.
Subtle memes by subtle means
Another curious piece of spyware, meanwhile, received commands through images. The malware communicated with its cybercriminal handlers through the most unlikely source: memes posted on Twitter.
Having gotten onto the victim’s computer, the malware opened the relevant tweet and pulled its instructions from the funny image. Among the commands were:
- Take a screenshot of the desktop,
- Collect information about running processes,
- Copy data from the clipboard,
- Write file names from the specified folder.
Image-based code
Media files can hide not just text, but chunks of malicious code, so other cybercriminals began to follow in the spies’ wake. Using steganography does not turn an image, video, or music track into full-fledged malware, but it can be used to hide a payload from antivirus scans.
In January, for example, attackers distributed an amusing banner through online ad networks. It contained no actual advertising, and looked like a small white rectangle. But inside was a script for execution in a browser. That’s right, scripts can be loaded into an advertising slot to allow, for example, companies to collect ad-viewing statistics.
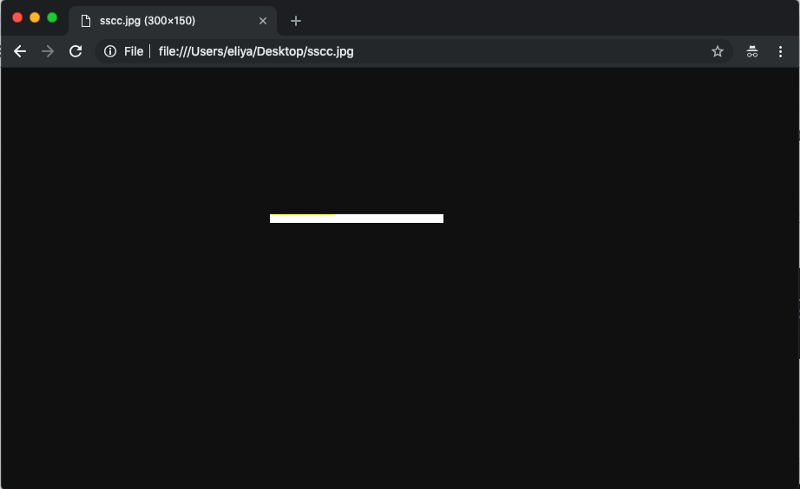
Banner with hidden code. Source: Confiant blog
The cybercriminals’ script recognized the color of the image pixels, and logged it as a set of letters and numbers. This would seem a rather pointless exercise, given that there was nothing to see but a white rectangle. However, seen through the eyes of the program, the pixels were not white, but almost white, and this “almost” was converted into malicious code, which was duly executed.
The code pulled from the picture redirected the user to the cybercriminals’ website. There, the victim was greeted by a Trojan disguised as an Adobe Flash Player update, which then downloaded other nastiness: in particular, adware.
Detecting steganography ain’t easy
As expert Simon Wiseman noted at RSA Conference 2018, quality steganography is extremely difficult to spot. And getting rid of it is also no picnic. Methods exist for embedding messages in images so deep that they remain even after printing and rescanning, resizing, or other editing.
However, as we already mentioned, information (including code) is extracted from images and videos using a special tool. In other words, media files by themselves do not steal or download anything from or to your computer. Therefore, you can secure your device by protecting it against malware components that hide text or malicious code in media files and extract it from them:
- Be in no hurry to open links and attachments in e-mails. Read the message carefully. If the sender’s address or the content looks dubious, better to ignore it.
- If you need to download something, always use trusted sources — for example, download apps from official stores or developer websites. The same goes for movies and music — do not download anything from unknown resources.
- Use a robust security solution. Even if it fails to recognize image-based code, it can catch suspicious actions by other malware modules.
 Technology
Technology

 Tips
Tips