Smart homes represent a young, yet full-fledged category of electronic goods. Kettles with a web interface, irons that switch off remotely, smart lighting control systems — it’s all been invented to make our lives easier. But are these products safe? Besides convenience, internet of things (IoT) devices bring new security and privacy risks, and it’s a rare week that passes without a report of another vulnerability in this or that smart gadget. Even a “smart light bulb” can be used to hack into a home network, never mind what can be done with more serious equipment.
A key element of any home security system is a video camera hooked up to the internet. They come in all flavors: from nanny cams and video doorbells to sophisticated motorized cameras for professional video surveillance.
IP cameras, as the name implies, are permanently online or connect periodically, and the footage is usually available via the vendor’s own specialized service. Logging into this service gives you access to the camera’s video stream wherever you are in the world. Besides being handy, the alternative — such as a camera accessible only from a local network — is unlikely to appeal to potential customers.
But this raises a host of questions, not least: what if cybercrooks steal your login credentials? How secure are cloud video surveillance systems? Can attackers access the video stream without hacking into your account? After all, if worse comes to worst, highly sensitive information, including images and videos of your home, will fall into the wrong hands.
Broken promises
All such fears were well known to Anker when it launched its own line of IP cameras under the Eufy brand. Founded in 2011, Anker is no newcomer to the electronics industry. Having started out making chargers and accessories for smartphones and laptops, it has gradually built up a full range of portable electronic devices to suit every taste and need, including its video doorbells and security cameras.
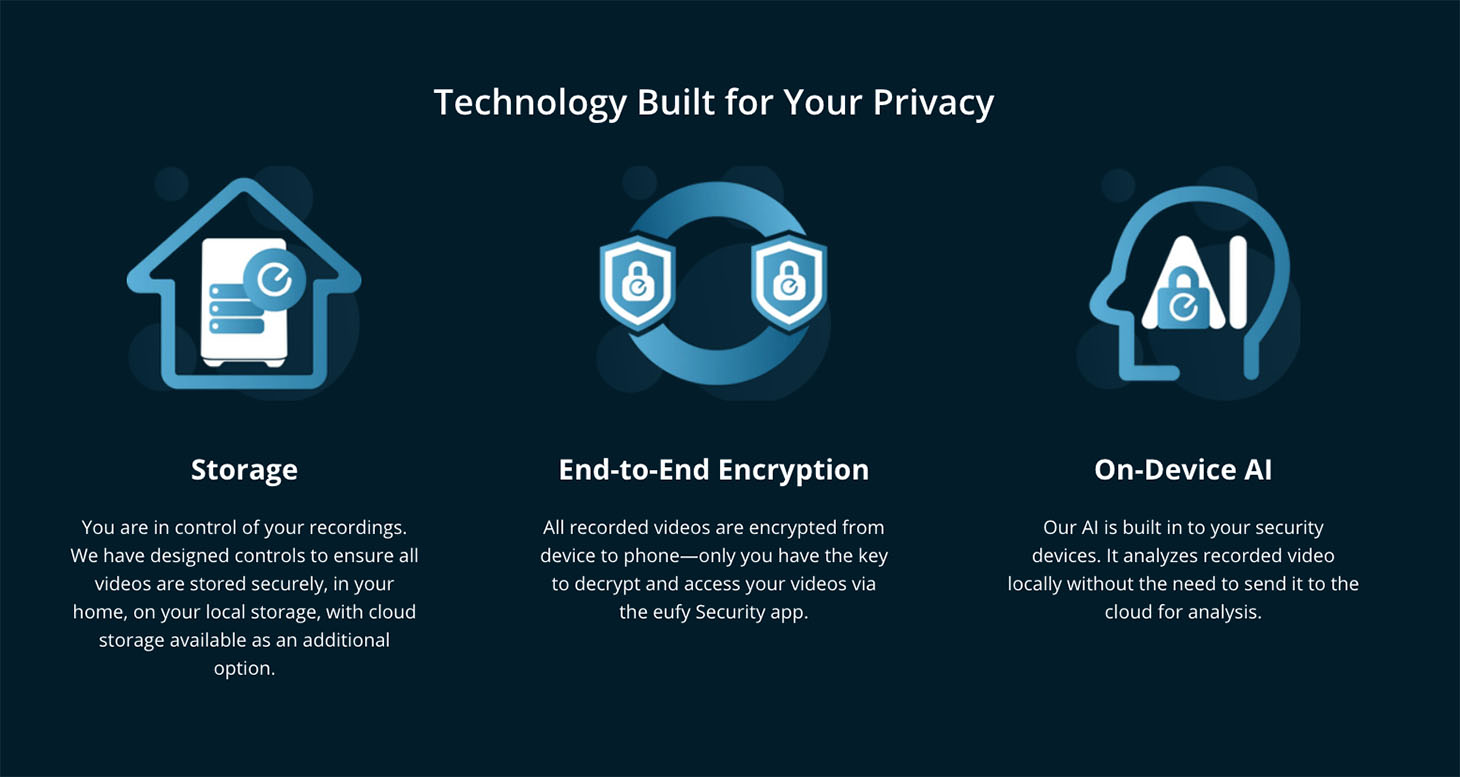
In an ad on the Eufy site, the camera developers guarantee maximal privacy and that no clouds are used: all data is kept in secure local storage. The remote video surveillance function can be completely disabled, but if you do fancy seeing what’s going on inside your home, the camera will encrypt the video stream and transmit it to an app on your smartphone — the only place where it will be decrypted. This is known as end-to-end encryption, meaning that no one — not even the vendor — can access the data.
Also important is that the recognition system works directly on the device itself. The built-in AI in each camera analyzes the footage without transmitting anything to the company’s servers, identifies people in the frame, and even distinguishes, say, landlords and tenants from strangers, so that the camera owner is notified only if an unfamiliar face comes into view.
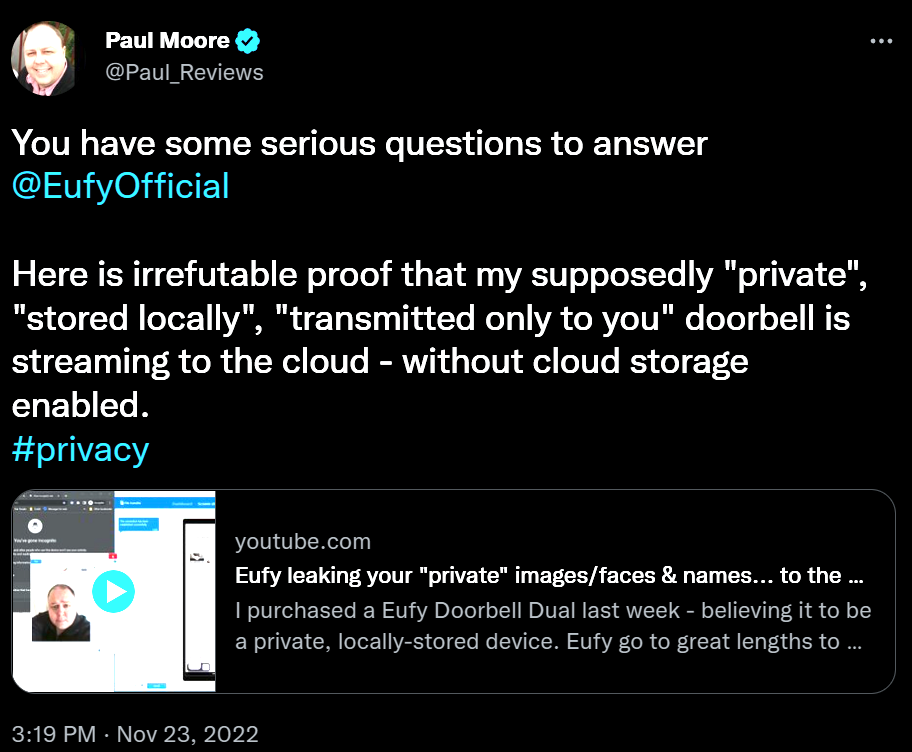
Total privacy — guaranteed. Users, however, were recently treated to a little surprise: Eufy cameras operate slightly differently behind the scenes. On November 23, British security expert Paul Moore tweeted a video accusing Eufy of transmitting data to the cloud — even when this option is disabled.
Moore’s video gives a detailed demonstration of the problem, which he detected quite easily. Having installed a Eufy video doorbell, Paul logged in to the device’s web interface, where he analyzed the source code in the browser and showed that the camera sends a picture to the vendor’s server every time someone appears in the frame. This means that at least one of Eufy’s guarantees (“no clouds”) isn’t true.
Moore then tweeted several more times about some far more serious data protection issues. Apparently, Eufy’s “reliable” encryption uses a fixed key identical for all users. Worse, this key actually appeared in Eufy code posted by the company itself on GitHub. Later, the tech website The Verge, with reference to Moore and another security expert, confirmed the worst-case scenario: anyone online, it seems, can view the video stream simply by connecting to a unique address of the device.
Fuzzy explanation
It should be said that there’s a completely logical explanation for the first issue of uploading footage to the cloud. In theory, Eufy cameras work as follows: you install the camera in your home, and configure the app on your smartphone. When someone presses the Smart Сall button, or the recognition system sees someone appear in the frame, you get a notification on your smartphone with a photo attached. The only way to send such notifications, most likely, is via the cloud. But why then did Eufy promise a cloudless experience? Good question!
And what about the video stream being accessible remotely? The Verge and its sources didn’t disclose all aspects of the problem — for fear the vulnerability could be mass-exploited. But some facts are known: first, the promised encryption isn’t used to transmit the video stream. In fact, the stream isn’t encrypted at all and can be viewed using a regular media player, such as VLC. Second, to access a particular camera, you need to know its unique URL; in other words — its address on the internet. But these addresses are generated in a predictable way: based on the device’s serial number printed directly on the box, plus the current date and time. Added to that (for extra “security”) is a random four-digit number, which is easy to brute-force. The only thing that saves the camera owner from an attacker who knows the serial number of the device is that the camera doesn’t constantly upload data online. It must first be activated, for example, by pressing the doorbell button, at which moment it becomes possible for an outsider to connect.
Anker, the maker of Eufy, was asked to confirm or deny the allegations, which only muddied the waters further. As noted by The Verge and Ars Technica, the developers flatly denied the existence of any security issues, and when asked about specific problems, they issued at least two statements that were later disproved.
In the first, the company “confirmed” that it was not possible to watch live footage from a camera, but The Verge did exactly that using two of its own Eufy cameras. In the second, the vendor admitted that footage from the doorbell gets sent to the company’s servers, but only to ensure that those same notifications are delivered to the smartphone, after which the images are deleted. But this also was disproved by Moore by means of a simple test: after viewing photos from the camera in his personal account, he saved the URLs of the images, then deleted them from his phone. Although the images disappeared from his personal account, Moore was able to access them simply by entering the saved URLs into the browser’s address bar. The other researcher went further: after doing a full reset of the video camera, which deleted all saved videos from his account, he re-linked the device to his account and saw… the supposedly deleted videos!
Generally speaking, certain ethical standards have evolved within the security industry, including how to disclose information about vulnerabilities and how vendors should respond. But in the case of Eufy, that all went out the window: instead of giving the company a chance to fix the issues, the researchers immediately went public with the vulnerabilities. Then, to add fuel to the fire, the company chose to deny the obvious issues. Eufy provided no technical evidence to refute the claims of the independent experts, while the only change that Moore noticed after his incriminating posts was that links to camera frames, previously shown in cleartext in the HTML, were now obfuscated. That is, the information is still sent to the Eufy server — only it became more difficult to trace.
Thus, the vendor broke another promise on its website, apparently hoping that no one would check. But this practice by Eufy violates not only the company’s promises, but also regional user data protection laws, such as the EU’s GDPR.
Protection methods
The Eufy case is still young, and additional research is needed to prove conclusively that an outsider can intercept footage from the IP camera of a particular user or a random one. However, there are examples of even more serious security issues. For instance, in 2021, IP cameras from Chinese manufacturer Hikvision were found to contain a critical vulnerability that gave an attacker full control over the device. A patch was released to fix it, but even a year later tens of thousands of video cameras worldwide were still vulnerable and accessible to any curious third party. Sadly, owners of such devices may not even be aware of the vulnerability, which is the worst-case scenario.
So, once more we’re confronted with those eternally posed questions: who’s to blame and what to do? Unfortunately, the IoT industry is hardly standardized at all. There are no generally accepted norms that would provide at least minimum security, and vendors protect their devices based on available resources and their own notions of security. It falls to the user to decide which vendor to trust.
As Ars Technica rightly points out, if your device has a lens and Wi-Fi, sooner or later someone will find a security hole in it. Interestingly, devices that are similar in terms of design — webcams in laptops and smartphones — are much better protected: an indicator lights up when the camera is in use, and security solutions monitor apps and block unauthorized access to it.
IP surveillance cameras, on the other hand, work autonomously, sometimes 24/7. Alas, until there appears a generally accepted system for evaluating device security, you shouldn’t rely on the “guarantees” of vendors, but take certain measures of your own to protect your privacy. We recommend that owners of any video surveillance system keep an eye out for news about security issues with their devices, carefully review the camera settings, turn off any unused cloud features, and install updates regularly. And when deciding to install a video surveillance system inside your home, weigh up all the risks — as the potential damage from hacking is clearly huge.
 threats
threats