Battle City, colloquially known as “that tank game”, is a symbol of a bygone era. Some 30 years ago, gamers would pop a cartridge into their console, settle in front of a bulky TV, and obliterate waves of enemy tanks until the screen gave out.
Today, the world’s a different place, but tank games remain popular. Modern iterations offer gamers not just the thrill of gameplay but also the chance to earn NFTs. Cybercriminals too have something to offer: a sophisticated attack targeting crypto-gaming enthusiasts.
Backdoor and zero-day exploit in Google Chrome
This story begins in February 2024, when our security solution detected the Manuscrypt backdoor on a user’s computer in Russia. We’re very familiar with this backdoor; various versions of it have been used by the Lazarus APT group since at least 2013. So, given we already know the main tool and methods used by the attackers — what’s so special about this particular incident?
The thing is that these hackers typically target large organizations like banks, IT companies, universities, and even government agencies. But this time, Lazarus hit an individual user, planting a backdoor on a personal computer! The cybercriminals lured the victim to a game site and thereby gained complete access to their system. Three things made this possible:
- The victim’s irresistible desire to play their favorite tank game in a new format
- A zero-day vulnerability in Google Chrome
- An exploit that allowed remote code execution in the Google Chrome process
Before you start to worry, relax: Google has since released a browser update, blocked the tank game’s website, and thanked the Kaspersky security researchers. But just in case, our products detect both the Manuscrypt backdoor and the exploit. We’ve delved into the details of this story on the Securelist blog.
Fake accounts
At the start of the investigation, we thought the group had gone to extraordinary lengths this time: “Did they actually create an entire game just for a scam?” But we soon worked out what they’d really done. The cybercriminals based their game — DeTankZone — on the existing game DeFiTankLand. They really went all out, stealing the source code of DeFiTankLand and creating fake social media accounts for their counterfeit.
Around the same time, in March 2024, the price of the DefitankLand (sic) cryptocurrency plummeted — the developers of the original game announced that their cold wallet had been hacked, and “someone” had stolen $20,000. The identity of this “someone” remains a mystery. The developers believe it was an insider, but we suspect that the ever-present tentacles of Lazarus are involved.
The cybercriminals orchestrated a full-blown promotion campaign for their game: they boosted follower counts on X (formerly Twitter), sent collaboration offers to hundreds of cryptocurrency influencers (also potential victims), created premium LinkedIn accounts, and organized waves of phishing emails. As a result, the fake game got even more traction than the original (6000 followers on X, versus 5000 for the original game’s account).
How we played tanks
Now for the most fun part…
The malicious site that Lazarus lured their victims to offered a chance, not only to “try out” a zero-day browser exploit, but also to play a beta version of the game. Now, here at Kaspersky, we respect the classics, so we couldn’t resist having a go on this promising new version. We downloaded an archive that seemed completely legitimate: 400MB in size, correct file structure, logos, UI elements, and 3D model textures. Boot her up!
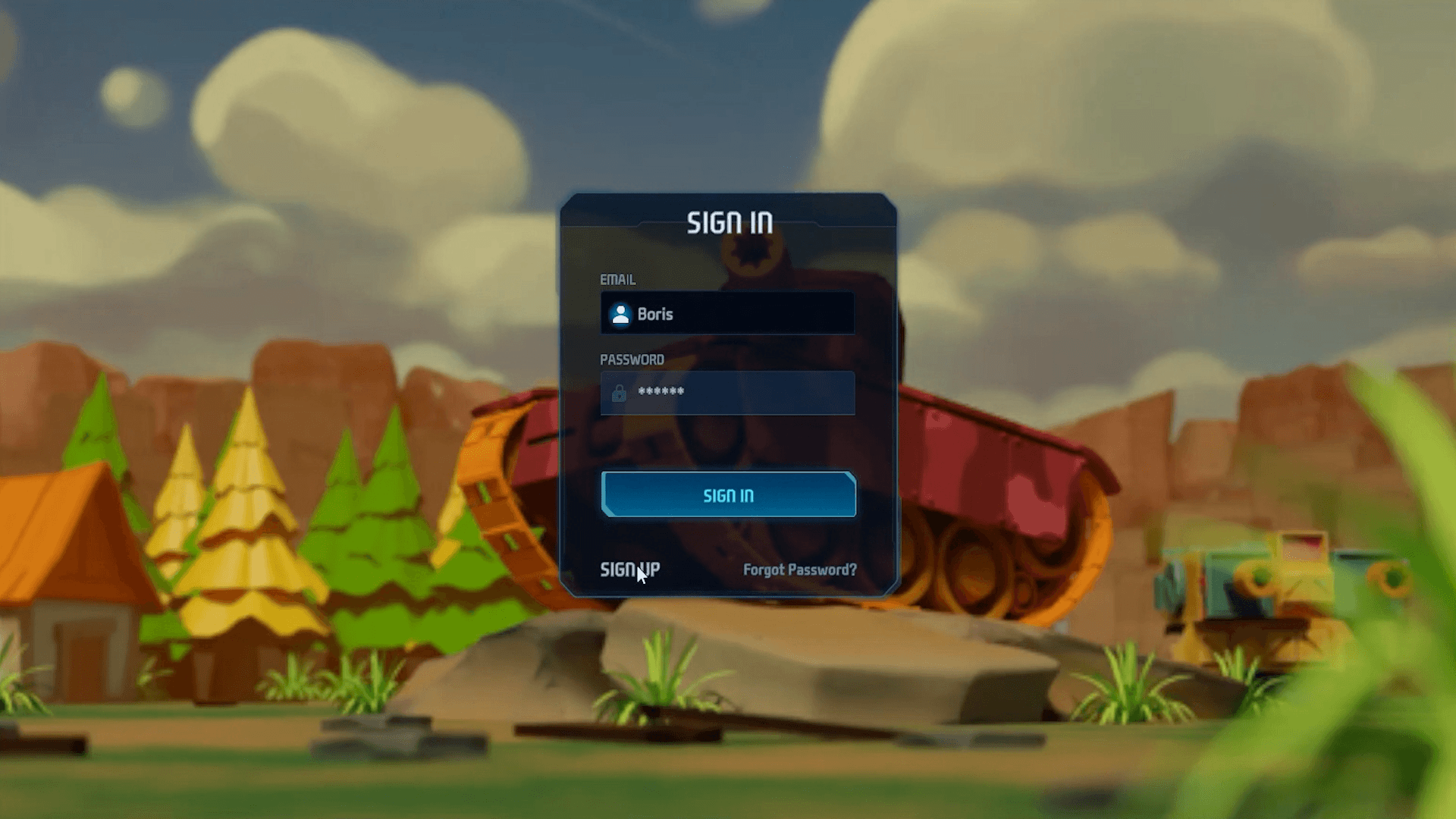
The DeTankZone start menu greeted us with a prompt to enter an email address and password. We first tried logging in using common passwords like “12345” and “password” but that doesn’t work. “Fine, then”, we think. “We’ll just register a new account”. Again, no luck — the system wouldn’t let us play.
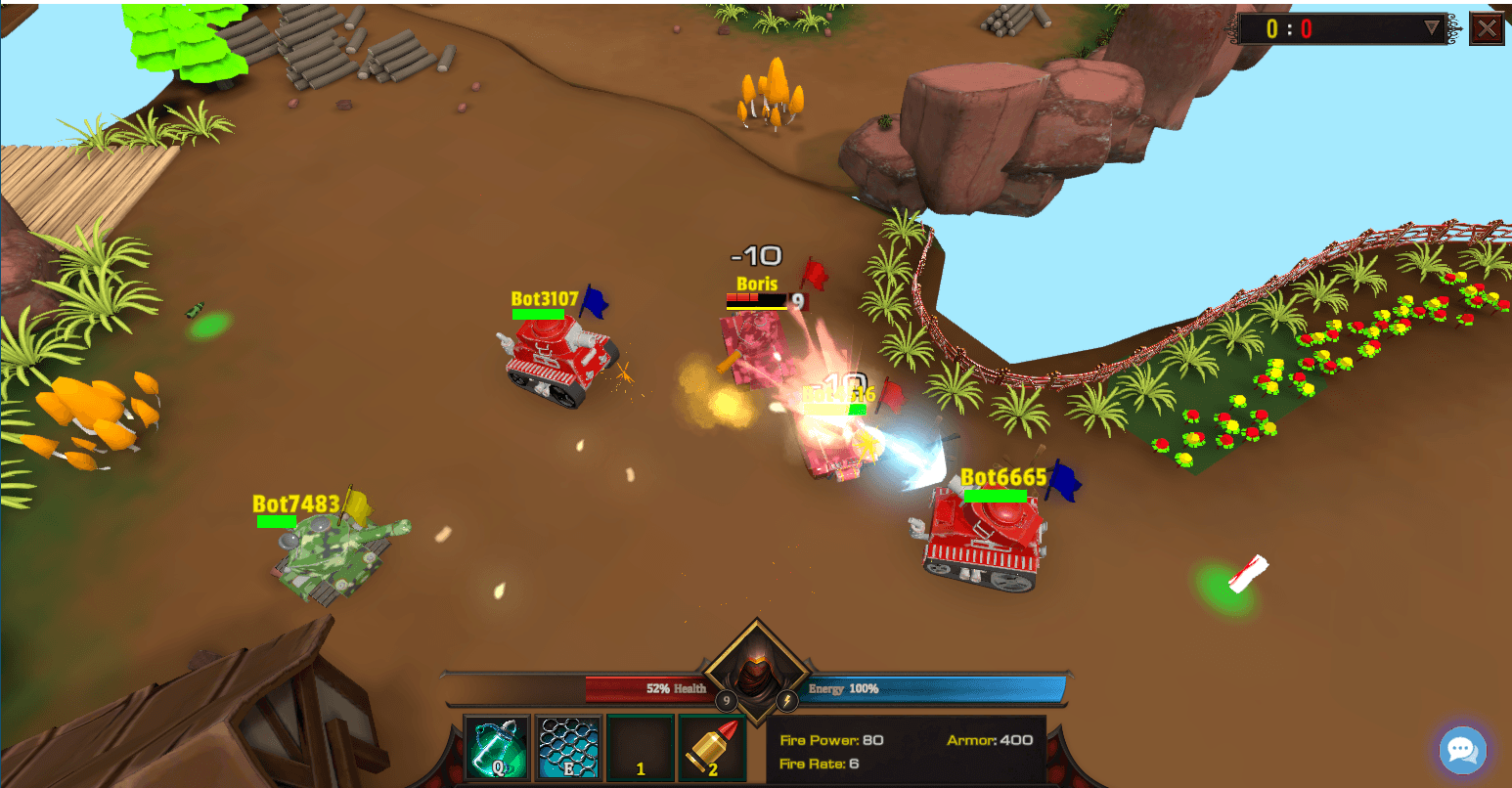
So why were there 3D model textures and other files in the game archive? Could they really have been other components of the malware? Actually, it wasn’t that bad. We reverse-engineered the code and discovered elements responsible for the connection to the game server — which, for this fake version, was non-functional. So, in theory, the game was still playable. A bit of time spent, a little programming, and voilà — we replace the hackers’ server with our own, and the red tank “Boris” enters the arena.
Lessons from this attack
The key takeaway here is that even seemingly harmless web links can end up with your entire computer being hijacked. Cybercriminals are constantly refining their tactics and methods. Lazarus is already using generative AI with some success, meaning we can expect even more sophisticated attacks involving it in the future.
Security solutions are also evolving with effective integration of AI — learn more here and here. All ordinary internet users have to do is make sure their devices are protected, and stay informed about the latest scams. Fortunately, the Kaspersky Daily blog makes this easy — subscribe to stay updated…
 scam
scam



 Tips
Tips