Imagine that one day you decide to use Bitcoin to pay for, say, a pizza. You copy the wallet address from the pizzeria’s website, enter the required amount, and click the Send button. The transfer goes through, but the pizza doesn’t arrives. The pizzeria owners say they never received the payment. What’s going on? Don’t get mad at the pizza guys — it’s all down to CryptoShuffler.
Unlike cryptoransomware, this Trojan avoids flashy effects, instead doing its best to slip under the radar. It resides quietly in the computer’s memory and monitors the clipboard — the temporary storage area for cut/paste operations.
As soon as CryptoShuffler spots the address of a cryptocurrency wallet on the clipboard (it’s quite easy to distinguish these addresses by line length and specific characters), it replaces the address with another. As a result, the cryptocurrency transfer does indeed go through, and in the amount specified by the payer, only the recipient is not the pizzeria, but the intruders behind CryptoShuffler.
Having studied the Trojan, Kaspersky Lab discovered that the malware targets not only Bitcoin, but also Ethereum, Zcash, Monero, Dash, Dogecoin (yes, it’s real), and other cryptocurrencies as well. Substituting Bitcoin wallets is the Trojan’s most lucrative activity — at the time of publication the attackers had snagged slightly more than 23 BTC (about $140,000 at the current exchange rate).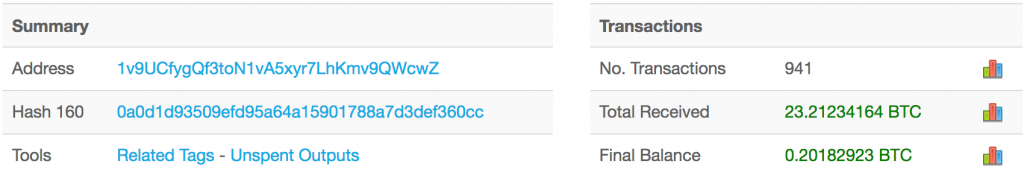
The other cryptocurrency wallets belonging to CryptoShuffler’s creators were found to contain sums ranging from tens to thousands of dollars.
It took the Trojan a little more than a year to collect that money. Peak activity in late 2016 was followed by a slump, but then in June 2017, CryptoShuffler reawakened.
This Trojan clearly demonstrates that an infected computer or smartphone will not necessarily slow down or display ransom messages. On the contrary, many kinds of malware try to keep a low profile and to operate as stealthily as possible; the longer they remain undetected, the more money they will make for their creators.
So our advice to all cryptocurrency users is to remain vigilant and get protected. Our products detect CryptoShuffler as Trojan-Banker.Win32.CryptoShuffler.gen, and, needless to say, block all its actions.
 bitcoin
bitcoin

 Tips
Tips