Israeli security researcher Mordechai Guri of Ben-Gurion University has published a study on yet another method of exfiltrating data from an air-gapped network. This time, he found a way to transmit data using radio waves from the CPU, more specifically from its power supply. This method of data exfiltration requires the attacker to be no more than a couple of meters from the CPU. This could not but remind Guri of the social distancing rules during the COVID-19 pandemic, hence the somewhat strange name, COVID-bit.
Guri tends to specialize in the most bizarre data exfiltration methods. He consistently researches the security of isolated computer networks, in which he clearly demonstrates the folly of relying solely on the air-gap method when building a security model. Most of the methods discovered by Guri and his colleagues work under certain conditions — when attackers have somehow managed to install spyware on a specially protected computer, and now need to extract the harvested data. And this needs to be done discreetly, without connecting to the internet and, where possible, by means of computer equipment already used by victim.
Switching converter as transmitter
This time, Guri explored the possibility of applying the operating principle of voltage switching to exfiltrate data. Any power supply for a phone or laptop is basically an AC-to-DC switching converter. Switch-mode power supplies are more compact than linear ones, but by their very nature emit a good deal of radio interference. Most of all, they irritate radio amateurs operating on medium and short waves, where the parasitic radiation of such power supplies is especially noticeable.
Similar voltage converters are present in many personal computers, some of which are used to power the CPU. All modern CPUs use a system of dynamic voltage and frequency variation. Such a system makes it possible to reduce power consumption when the CPU is idle: you can lower its frequency and voltage, then raise them sharply when a new computational task comes along.
Since in the studied scenario the attacker already controls the victim’s computer with malware, they are able to manipulate the CPU load in some way, and with it the frequency and voltage. But how? Guri found that the parasitic radiation of a switching voltage converter changes form when the operating voltage is altered. And the voltage varies depending on the load. That is, by applying a load to the CPU at a specific interval, you can generate a radio signal at a certain frequency.
The signal transmission frequency can be set by alternately loading and unloading the CPU at this specific interval, thousands of times per second. The type of load (that is, what the CPU is asked to compute) does not matter: it is run for no other reason than to generate a radio signal of a certain shape. The CPU under load requires a change in the supply voltage, the voltage converter creates radio interference, and the conductors on the motherboard act as an antenna. Here’s what the resulting radio signal looks like:
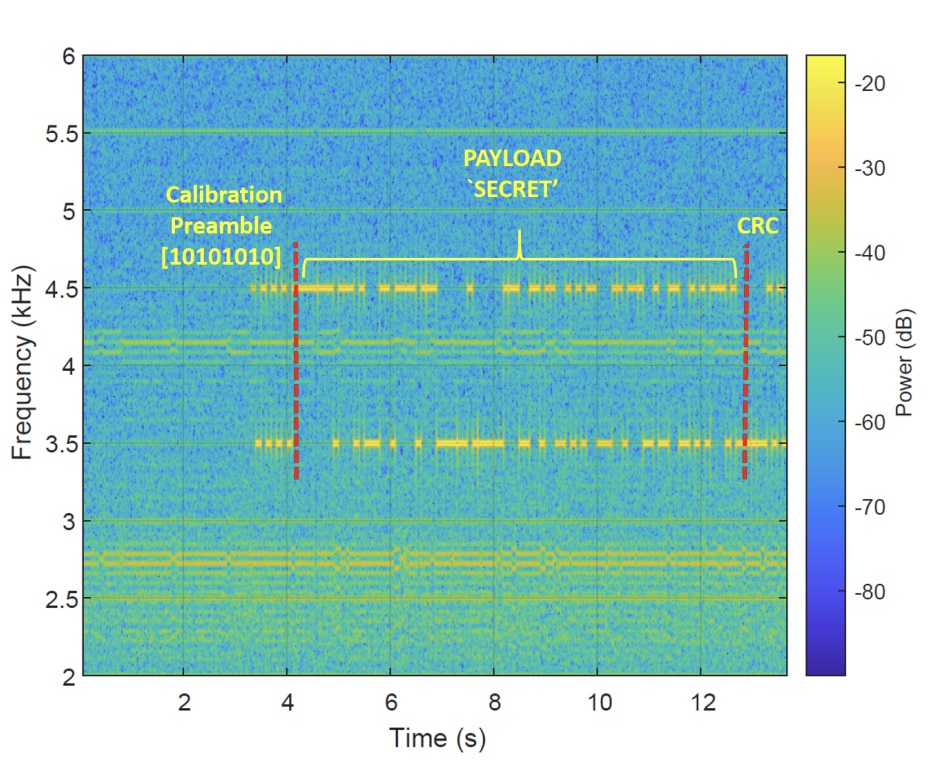
Spectral representation of a computer-emitted radio signal. Source.
The image shows the spectrum of a radio signal with a frequency of 2 to 6 kilohertz. For data transmission, the frequency-shift keying method is used, whereby the frequency of the signal varies depending on the data transmitted. That’s the reason we see two “lines” of transmission at different frequencies. The color, ranging from green to red, indicates the power, from which we can conclude that the radio signal from the CPU is quite weak, only slightly stronger than the interference seen at the bottom of the image. Note the timeline: the word “SECRET” is transmitted for approximately 10 seconds. This method of stealing data is very slow, but for certain types of sensitive information, it may suffice. If necessary, the transmission rate can be increased by loading several CPU cores simultaneously (but differently).
Receiving secrets by phone
Guri also discusses in detail the issue of reception. A low-power radio signal can in reality be received at a distance of no more than 2 meters from an isolated system.

COVID-bit data theft scenario: an attacker moves within the minimum distance from the computer without drawing attention. Source.
The figure shows one of the possible scenarios: an attacker visits the victim’s office and extracts secret information from an infected machine. The data exfiltration can also be performed by a bribed employee of the target organization. In either case, it is unlikely that the attackers will be able to carry bulky radio gear with them, which is why the study highlights a method for receiving classified information via smartphone.
Most smartphones are not equipped with a medium-wave radio receiver, but it’s possible to make do with an audio chip. An analog-to-digital converter in the smartphone is capable of digitizing radio waves with a frequency of up to 24 kilohertz, so one has to insert an antenna into the headset jack. It might not be ideal, but as practice shows, it gets the job done.
The resulted data exfiltration technique is fairly effective (by the standards of attacks on protected isolated systems, of course). Besides the “slow” form of data theft shown above, Guri also tested out faster transmission methods, some of which hit speeds of up to 1000 bps. This is enough to transfer an IP address in an instant, an encryption key in 4 seconds, and small files in minutes.
Anti-spy activity
The study dutifully lists potential ways to counteract this method of exfiltration. The simplest is that same social distancing — not letting outsiders nearer than 2 meters to protected computers. And then there are some slightly more complex ones: you can, for example, stifle the data transfer by loading the CPU with your own tasks. This wastes energy, but reliably prevents leakage. Interestingly, locking the CPU on a particular frequency, despite reducing the signal power, does not rule out data transmission. The varying load on the CPU produces interference that can still help a spy, even at a constant frequency.
It is even more useless to attempt to track the covert transmission of radio signals: it is too similar to the normal operation of computer hardware. Guri demonstrates that for every way to increase the isolation of a computer, there is a new method of exfiltrating data through third-party channels. Too many things inside the computer generate interference and background noise, which can be manipulated. Far better simply to accept as a fact that an air gap in itself does not deliver total security. You neutralize the risk of an attack from the internet, but not other forms of cyberattacks. This means that effective protection of isolated systems is impossible without tools for detecting and defanging malware. Or rather without a comprehensive security system that takes into account all aspects of a dedicated secure network.
 air gap
air gap

 Tips
Tips