The last weekend of this summer was marked by an internet-wide newsbreak: anonymous hackers (perhaps a single man) somehow obtained explicit photos of various Hollywood celebrities, including many A-listers, like Jennifer Lawrence, and publicized this material on the Internet. Such leaks are not new, however, this one was on a massive scale. From the very beginning there was an assumption that perhaps some photos were stolen directly from celebrities’ accounts in the Apple’s iCloud. Is this possible? If so, what can be done to avoid the theft?
Possible leak scenario
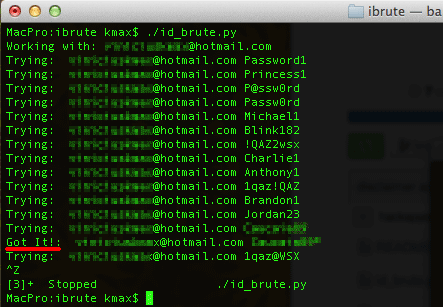
At this time, there is no hard evidence in this case. Apple and the FBI are currently investigating and we look forward to reading the results. Some facts suggest that unauthorized access to victims’ accounts was possible due to a combination of factors. First, a small flaw in the iCloud platform implementation allowed an unlimited amount of account password tries. Normally, a web service locks the account when someone unsuccessfully tries to log in more than 3-5 times. While that was the case for the normal web interface of iCloud, the Find My iPhone interface was lacking this limitation. This defect enabled hypothetical hackers to implement “bruteforcing”, i.e. systematically trying multiple popular passwords until they give up or the access is granted. To bruteforce iCloud accounts, hackers may have used an open source application, which emerged on the popular programmers’ site, GitHub, just a few days before the incident.
Second, many celebrities probably ignored strong password policies and chose very basic passwords. Hackers may have only tried the top-500 popular passwords for bruteforcing and could have still achieved impressive results.
Third, and this is most important, Apple provides a protection from such attacks by implementing two-factor authentication. Needless to say, victims undeservedly neglected this effective tool as well.
According to some reports, the flaw was promptly fixed, and by Monday it was impossible to bruteforce iCloud accounts anymore. However, there are no guarantees that other vulnerabilities do not exist.
Furthermore, this is not the first occasion when criminals have attacked Apple users utilizing iCloud and Find My iPhone. This summer, some countries experienced a wave of cyber-extortion incidents were victims suddenly found their iPhones/iPads locked using the anti-theft functionality of Find My iPhone. The lock screen was displaying a message demanding a ransom to regain control of the device.
Protecting yourself and your data
This alleged incident proves that our privacy is increasingly fragile nowadays, for celebs and ordinary people alike. Although cloud-based file storage services have long been popular among Internet users, the indisputable convenience of such services is at least partly offset by some significant risks.
For example, many users store scans of their passports and other sensitive documents (or sensitive photos) in the cloud – though sometimes vulnerabilities in the service jeopardize the security of that personal data. When it comes to cloud security, the security of the endpoint is often overlooked. The device itself could also become the source of a leak if it is compromised by malware with spying capabilities that can sends files and credentials from the cloud directly into the hands of cybercriminals.
To avoid possible issues with private data leaks via computers, mobile devices or cloud services, Christian Funk, Senior Security Researcher at Kaspersky Lab, recommends the following measures:
- Use strong passwords, unique to each account.
- Use endpoint security solutions to protect your devices, because every device is a gateway to your cloud storage.
- Enable and use two-factor authentication services whenever available.
- Sort out which information should or should not be stored in the cloud. Your most sensitive information – whether relating to your personal or professional life – should never be trusted to the cloud.
- It’s easy for a mobile device to be lost or stolen, so make sure the device itself has no sensitive data stored on it. If this is impossible, make sure there is appropriate encryption in place.
- If you’re about to store highly sensitive information (including photos and videos), double check that your device doesn’t automatically upload data into the cloud.
- Before sharing your personal data or allowing someone to take a picture of you, make sure that the other device is sufficiently secure to keep your private data safe from inadvertent exposure.
7 tips from #Kaspersky experts on how to avoid #iCloud photo #leaks
Tweet
 apple
apple

 Tips
Tips