Parental Controls to Prevent In-App Purchases
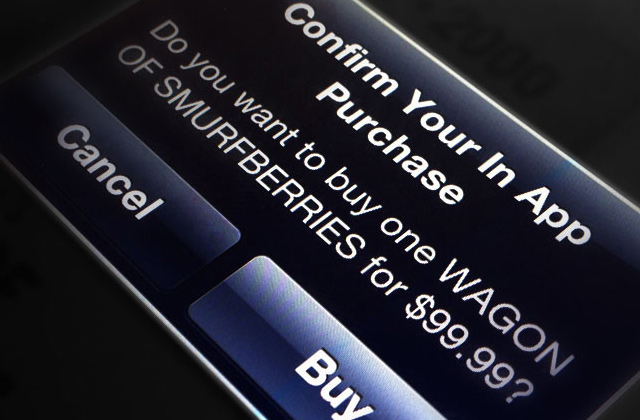
In-app purchases are the Holy Grail of revenue for app producers, especially those who make free gaming apps. The hook is that you love the game so much once you
617 articles

In-app purchases are the Holy Grail of revenue for app producers, especially those who make free gaming apps. The hook is that you love the game so much once you

In the U.S. many organizations offer the day after Thanksgiving, which falls on a Thursday, to their workers as a holiday. Brick and mortar American retailers have capitalized on this

For many Americans, November invokes images of turkey, pie and time spent with family, but for a great deal of others this time of year also brings up something very

You have always had Kaspersky Anti-Virus installed on your computer and have been satisfied with the basic protection you’ve received against common threats. You have started to use Internet banking

If you’re a registered Adobe client, change your passwords now. They have been stolen and published on the Internet, someone even made a crossword puzzle out of them. This is

Do you like our products for home use, but want to ensure the same high level of protection for the computers in your home office or small business? If your

As the recent NSA leaks have revealed, our digital lives make it very difficult to maintain anonymity and protect our privacy — especially since we tend to make it especially

Have you ever performed ritual dances calling to the gods to make your battery last five more minutes? We understand your concern and would like to offer an option that

Thousands of new viruses, Trojans, and other malicious programs appear every day. The information about these threats and ways of neutralizing them is contained in the databases of Kaspersky Internet

The safety and security of your personal computer is almost certainly something you’ve been dealing with for a long time. If you keep your anti-virus software updated and establish strong

All of us have heard a lot about numerous ways of stealing pin-codes for bank cards, so now we almost automatically check for key sheets, spy cams, etc. before we

If you have been following the latest in news, you’ve probably heard a lot of stories talking about privacy, information leakage, espionage and such. Given that most of our communications

Does your anti-virus seem to slow down your computer’s performance? When applications are lagging, you start randomly changing the anti-virus settings in order to fix the problem, don’t you? There

Gaming has been around for decades, and with all of the new advancements that have been made in technology throughout the years have come advancements in the way we game.

Do you have a personal computer at home that is not actually personal because it is meant for family use? Do your loved ones use it for work and Internet

There are potential risks that we all face online. These include malware, phishing scams and junk-mail. But there’s an added dimension where children are concerned. They’re less worldly-wise, so they

Our anti-virus products are constantly being tested and improved. Even when a product has been released, we continue to work on updating our packages. Our updates are always aimed at

In our past posts we mentioned ways to optimize your computer’s resources when Kaspersky Internet Security is active, in How To Configure A Kaspersky Product To Increase Computer Performance? and

If your kids haven’t gone back to school yet, they’re about to. That means school lunches, riding the bus and, of course, homework, are the norms again. And homework, of

In the previous ‘Tip Of The Week’ we found out How To Configure A Kaspersky Product To Increase Computer Performance. Today we’d like to revisit this subject and show you

Help recognize all that seniors have done and still are doing by helping them be more productive and healthy than ever with a rundown of great apps geared for older